Author: Ivan Ninichuck
Introduction:
In the dynamic landscape of cybersecurity, efficient incident response is paramount. Well-designed playbooks serve as critical automated workflows, significantly streamlining Security Operations (SecOps) and empowering analysts to operate with greater precision and effectiveness. Drawing from recent insights and industry best practices, this guide will explore key considerations for developing impactful and resilient playbooks.
Concept:
Playbooks Drive Your Case Management
Did you know your playbooks directly influence how your case management screen looks and functions? It's true! You can tailor things like:
-
Case Stages: Define the steps an alert goes through, like "triage".
-
Alert Overviews: Customize how initial alert information is displayed.
-
Closed case: Add additional root causes for case closure.
This level of customization means your platform can truly adapt to your unique SecOps workflows.
Turning Manual Steps and SOPs into Automated Playbooks
So, you've got your existing Standard Operating Procedures (SOPs) and manual investigation steps. How do you transform these into slick, automated playbooks? It's all about discovery and structured design!
The process often begins with discovery sessions. This is where your security advisors sit down with your SOC leadership and senior analysts. During these discussions, you'll delve deep into:
-
Your Current Objectives: What are you hoping to achieve? Are you migrating existing use cases, or starting fresh?
-
Top Threats: What are the biggest threats your organization faces, and what do you want to address in your initial "Minimum Viable Product" (MVP) playbooks?
-
Data Readiness: Which data sources are already good to go for onboarding?
-
Team Structure and Procedures: How is your team organized? Do you use an MSSP? How do different teams communicate during an investigation?
-
Current Investigation Steps: This is key! Walk through your current manual or semi-automated investigation steps, from start to finish. Make sure to ask about how you handle both false positives and true positives.
-
Escalation Paths: Understand if there are different tiers or groups of analysts who receive escalated cases.
-
Defining an Incident: Get a solid, shared understanding of what your organization considers a security incident.
This initial discovery is crucial because it provides all the information you need to begin building your playbooks, starting with the catch-all. You'll also gain insight into how to incorporate communication steps between teams for escalation and when remediation actions should take place.
When creating your first draft of the playbook design, remember that the catch-all playbook will include all enrichment steps, analyst assessment, escalation, and movement into the investigation stage if needed. For other playbooks, you can duplicate from the catch-all and simply add the unique remediation steps. If you don't have specific remediation steps defined, you can add the most logical ones (like "change password" or "isolate host") and set them to be manually executed. This gives your team the option to test them and helps alleviate any anxiety about automation.
Finally, during the design review meetings, you'll walk through each use case step-by-step with the customer. Explain that while playbooks may look similar, this consistency provides repeatable procedures, reduces analyst errors, and makes future playbook creation much more scalable. Make sure to emphasize that remediation actions set to manual can be skipped by the analyst, but by including them, the capability exists. This is a great way to ease concerns about full automation.
Your First Playbook? The "Catch-all" is Your Best Friend!
If you're wondering where to start, the answer is simple: build the "catchall playbook" first. This isn't just a suggestion; it's a necessity! Here's why it's so vital:
-
Basic Case Management Structure: The catch-all playbook has the core structure of your case management process
-
Universal Enrichment: Even if a specific playbook doesn't apply, the catch-all ensures your alerts still get enriched. This means you'll always have some context, preventing those "unassigned" cases from piling up.
Think of it as your safety net, catching anything that falls through the cracks and providing a solid starting point for investigation. Plus, once you have this in place, you can often duplicate it and just add the unique remediation steps for other specific use cases.
Catch-All Playbook Demonstration Outline
This outline provides a structured overview of a typical "Catch-All" playbook, designed to process all incoming alerts, ensure basic enrichment, and guide initial analyst assessment.
Playbook Trigger:
-
Configuration: Playbook triggers will be set to "all" with a level 3 priority.
-
Note: All other specific playbooks should be configured with at least a level 2 priority to ensure they are triggered before this catch-all playbook when a more specific trigger is available.
Playbook Flow:
-
Set Case Stage to "Triage"
-
This marks the initial phase of alert handling.
-
Get Similar Cases
-
Identify and link any previously observed similar incidents to provide context.
-
Run Identity Enrichment Block
-
Execute a reusable block to gather additional context and details related to any identities involved in the alert (e.g., user accounts, device identities).
-
Enrich Entities with Endpoint Data
-
Pull relevant information from endpoint security tools (e.g., process data, network connections, file hashes) for any entities identified in the alert.
-
Run Threat Data Enrichment Blocks
-
Execute reusable blocks to query external threat intelligence sources (e.g., VirusTotal, reputation services) for indicators found in the alert.
-
Set Case Stage to "Assessment"
-
Transition the case to the analyst review phase.
-
Multiple Choice Question: "Should the alert investigation be escalated?"
-
This interactive step prompts the analyst for a decision point.
-
No Branch (If Analyst Selects "No"):
-
Add Case Tag: "False Positive"
-
Close Alert
-
Playbook Ends
-
Yes Branch (If Analyst Selects "Yes"):
-
Tag: "Escalated"
-
Run Escalation Block
-
Execute a reusable block to initiate escalation procedures (e.g., notify higher-tier analysts, create tickets in other systems).
-
Playbook Continues
-
Set Case Stage to "Investigation"
-
Advance the case to a deeper investigation phase after escalation.
-
Close Alert
-
Finalize the alert process.
-
Playbook Ends
Playbook Setup Guide
You will need to navigate to the response section of the SecOps menu and choose playbooks. Once there you will be able to use the plus sign shown in this image to create a new playbook. You will choose the folder and environment for the playbook.
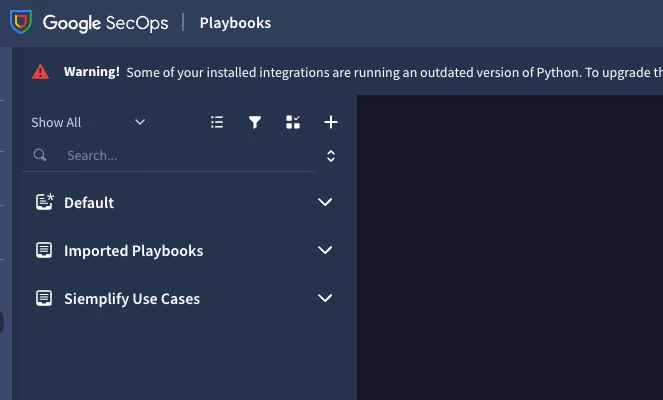
Playbook Trigger Configuration
First, you'll need to configure the playbook's trigger:
-
Set Playbook Trigger: Drag the Playbook Trigger configuration and drop it into the trigger section. Configure it to "all" with a level 3 priority.
- Note: Ensure all other specific playbooks are configured with at least a level 2 priority. This makes sure they are triggered before this general playbook when a more specific trigger is available.
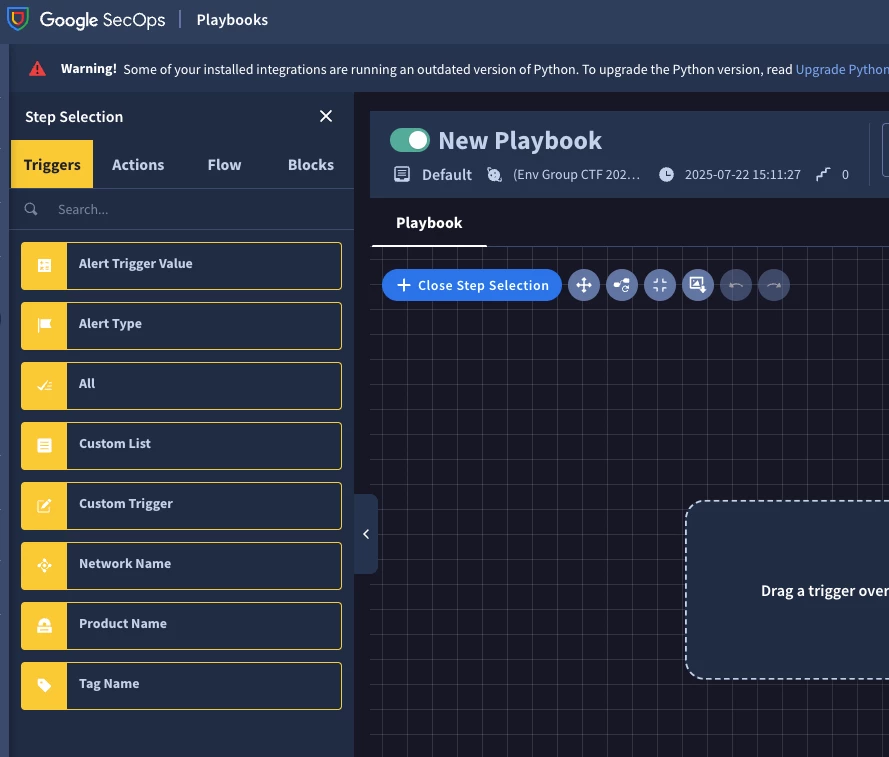
Playbook Flow
Now, let's build the main flow of your playbook: Click on the actions option that is next to triggers. Use the search box to find each action by typing in the name.
-
Set Case Stage to "Triage": Drag the "Change Case Stage” action and drop it next to the previous action.
-
This marks the initial phase of alert handling.
-
Double click the action and choose triage from the drop down menu
-
-
Get Similar Cases: Drag the "Get Similar Cases" action and drop it next to the previous action.
-
This identifies and links any previously observed similar incidents to provide context.
-
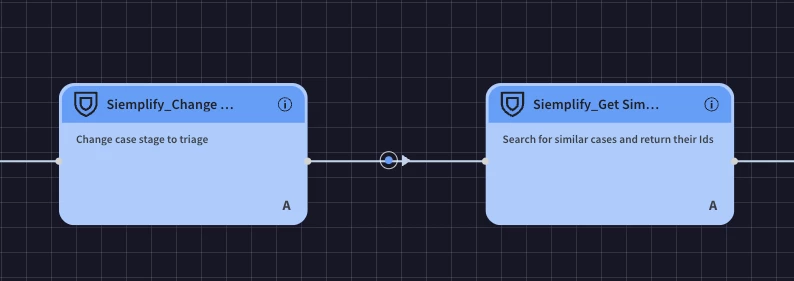
-
Run Identity Enrichment Block: Drag the "Run Identity Enrichment Block" action and drop it next to the previous action.
-
This executes a reusable block to gather additional context and details related to any identities involved in the alert (e.g., user accounts, device identities).
-
You will build these blocks separately from the main playbook.
-
In an identity enrichment block you might use either the Active Directory or Okta integrations to gather use information
-
-
Run Threat Data Enrichment Blocks: Drag the "Run Threat Data Enrichment Blocks" action and drop it next to the previous action.
This executes reusable blocks to query external threat intelligence sources (e.g., VirusTotal, reputation services) for indicators found in the alert.
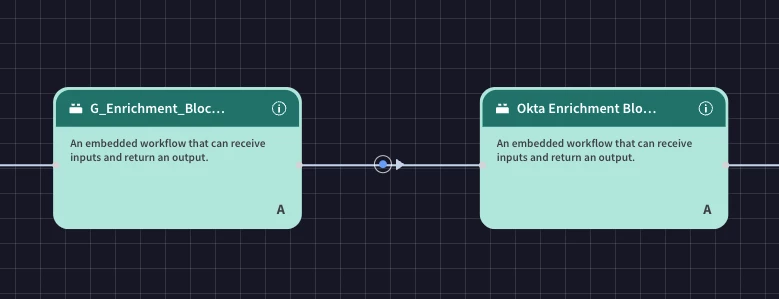
-
Enrich Entities with Endpoint Data: Drag the "Enrich Entities with Endpoint Data" action and drop it next to the previous action.
-
This pulls relevant information from endpoint security tools (e.g., process data, network connections, file hashes) for any entities identified in the alert.
-
-
Set Case Stage to "Assessment": Drag the "Change Case Stage” action and drop it next to the previous action. Double click the action and choose assessment.
-
This transitions the case to the analyst review phase.
-
-
Add Multiple Choice Question: Drag the "Multiple Choice Question" action and drop it next to the previous action.
-
Configure the question as: "Should the alert investigation be escalated?" This interactive step prompts the analyst for a decision point.
-
FLOW Branches
Depending on the analyst's answer to the "Multiple Choice Question," the playbook will follow one of two branches:
If Analyst Selects "No" (No Branch):
-
Add Case Tag: "False Positive": Drag the "Add Case Tag: 'False Positive'" action and drop it under the "No" branch of the multiple-choice question.
-
Close Alert: Drag the "Close Alert" action and drop it next to the previous action.
-
The playbook ends here.
If Analyst Selects "Yes" (Yes Branch):
-
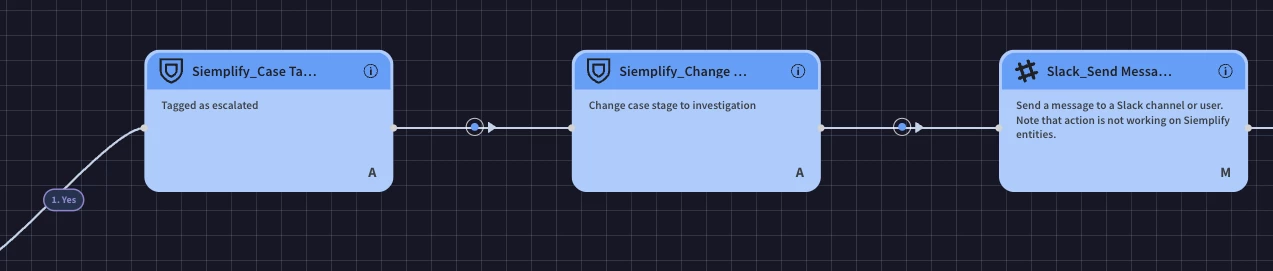
Add Tag: "Escalated": Drag the "Add Case Tag” action and drop it under the "Yes" branch of the multiple-choice question. Double click the action and enter escalated as the case tag.
-
Run Escalation Action: Drag the action to communicate the escalation and drop it next to the previous action.
-
This executes a reusable block to initiate escalation procedures (e.g., notify higher-tier analysts, create tickets in other systems).
-
Set Case Stage to "Investigation": Drag the "Set Case Stage” action and drop it next to the previous action. Double click the action and select “investigation”.
-
This advances the case to a deeper investigation phase after escalation.
-
Add Multiple Choice Question: Drag the "Multiple Choice Question" action and drop it next to the previous action.
-
Configure the question as: "Is this a true positive?" This interactive step prompts the analyst for a decision point.
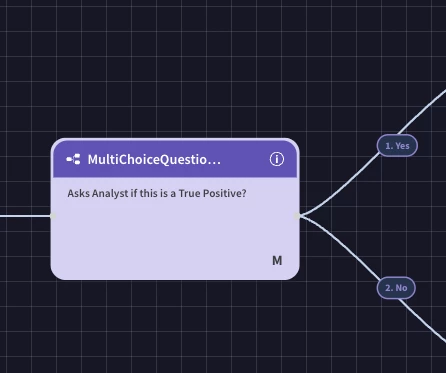
If Analyst Selects "No" (No Branch):
-
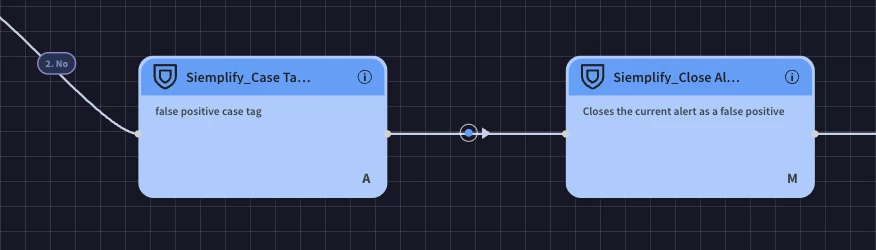
Add Case Tag: "False Positive": Drag the "Add Case Tag. (Double click the action and enter 'False Positive') action and drop it under the "No" branch of the multiple-choice question.
-
Close Alert: Drag the "Close Alert" action and drop it next to the previous action.
-
The playbook ends here.
If Analyst Selects "Yes" (Yes Branch):
-
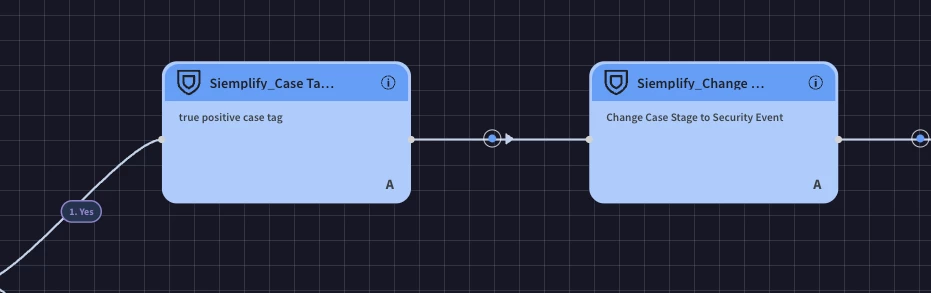
Add Tag: "True Positive": Drag the "Add Case Tag” action and drop it under the "Yes" branch of the multiple-choice question. Double click the action and write true positive as the tag.
-
Set Case Stage to "Investigation": Drag the "Change Case Stage” action and drop it next to the previous action. Double click the action and select “Security Event”. (Security Event is a custom case stage added in SOAR Settings. You can choose any stage name your organization wants to use here)
-
Close Alert: Drag the "Close Alert" action and drop it next to the previous action.
-
This finalizes the alert process, and the playbook ends.
Separate and Conquer with Environments
If you're dealing with multiple tenants, different teams, or distinct use cases (like physical security logs!), environments are your secret sauce. They let you keep things neatly separated, including:
-
Cases
-
Integration Instances
-
Playbooks (you can even separate these optionally!)
This is a game-changer, especially for Managed Security Service Providers (MSSPs).
Embrace Reusable Blocks: Think "Mini-Playbooks"
Imagine having a common action, like querying VirusTotal for every alert. Instead of building that step into every single playbook, use reusable blocks. These are like little sub-routines or functions in programming – small, modular playbooks within a larger one. They save you tons of time and keep your playbooks clean and efficient.
Thoughtful Creation and Trigger Configuration
When you're bringing a new playbook to life:
-
Start Disabled: Always create it turned off initially. Test before you unleash!
-
Clear Naming: Give it a descriptive name so everyone knows what it does.
-
Trigger Priority Matters: Your catchall playbook should use the "all" trigger with a priority of three, while most other playbooks should use a priority of two, leaving room for higher-priority use cases later on.
-
Go Custom with Triggers: While predefined options exist, custom triggers offer far more flexibility. Each use case should have a clear trigger.
Understanding the Power of Tags
Tags are set within the SOAR platform itself. While their role in initial alert handling has shifted a bit due to unified data schemas, they're still incredibly powerful within your playbooks for:
-
Customizing Reporting: Tailor your reports based on specific actions taken.
-
Dashboarding: Build insightful dashboards that reflect your playbook's operations.
Analysts Aren't Going Anywhere – Empower Them!
The goal of automation isn't to replace your analysts; it's to empower them! Your playbooks should seamlessly integrate human interaction. This means including steps that:
-
Ask Questions: Prompt analysts for their input.
-
Require Pending Actions: For when manual review or approval is needed.
-
Assign Manual Tasks: Direct specific tasks to individuals or roles.
It's about providing a standardized, efficient workflow that frees up analysts for deeper investigations.
Don't Lose Information When Closing Alerts
Closing alerts, especially through automation, needs careful thought to avoid losing valuable information.
-
False Positives: Once you've tested thoroughly, automation here is great! Just make sure you use placeholders to include all the relevant Unified Data Model (UDM) event details.
-
True Positives: For actual incidents, implement manual closure steps. This ensures analysts provide crucial investigation notes, root cause analysis, and other important context.
Don't Just Start Coding, Start Designing!
Think of it like building a house – you wouldn't just start laying bricks without a blueprint, right? The same goes for playbooks. Before you even think about automation, create a use case design document. This isn't just busywork; it's your foundation. This document should clearly lay out:
-
Who's involved? (Your "contacts" in the lingo).
-
Where's the data coming from? (Your "data sources" – you can even link to a separate doc for this).
-
What detections are we looking for? (Both your pre-built "curated" ones and your custom rules).
-
What tools will we be hooking up? (Your "integrations").
-
Interested in leveraging AI for Google Secops? Watch this video
This document is super helpful for visualizing every step the playbook will take, and it ensures everyone's on the same page about how to handle both real threats and those pesky false alarms. It's about getting that "scope lock" before you begin.
By diligently applying these best practices—from initial design and the strategic use of a catch-all playbook to the thoughtful integration of automation and human insight—your organization can build a robust and highly efficient SecOps capability. This proactive approach not only streamlines incident response but also fosters a more resilient security posture, ultimately empowering your team to navigate the complex threat landscape with greater confidence and control.
