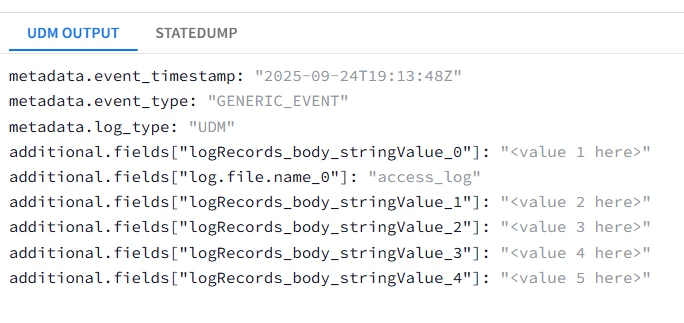
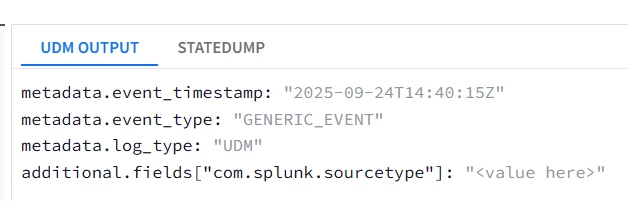
Hello! I am struggling with how to handle nested arrays in my parsers. I have been reviewing the following documentation but I still am unable to full wrap my head around how to make it all work. I have the following JSON log (its a lot longer but I just want to see how to start it)
"resourceLogs": [
{
"resource": {
"attributes": [
{
"key": "com.splunk.sourcetype",
"value": {
"stringValue": "<value here>"
}
},
{
"key": "host.name",
"value": {
"stringValue": "<value here>"
}
},
{
"key": "os.type",
"value": {
"stringValue": "linux"
}
}
]
},And following the documentation I conjured up the following but I continue to run into generic errors, I havent include the “host.name” or the “os.type” yet because I wasnt able to get the “source_type” out of the log:
filter {
# Parse JSON
json {
source => "message"
array_function => "split_columns"
on_error => "_not_json"
}
if [_not_json] {
drop { tag => "TAG_MALFORMED_MESSAGE"}
}
for index, resource_log in resourceLogs {
for idx, attr in resource_log.resource.attributes {
# This doesn't work
mutate {
replace => {
"source_type" => ""
"host_name" => ""
"os_type" => ""
}
}
# I dont think I am handling this correctly
if attr == "com.splunk.sourcetype" {
mutate {
replace => {
"source_type.key" = "%{key}"
"source_type.value.string_value" => "%source_type"
}
}
mutate {
merge => {
"udm_event.idm.read_only_udm.additional.fields" => "source_type"
}
}
}
}
}
mutate {
replace => {
"@output" => ["udm_event"]
}
}
}
Any assistance would be wonder - these logs are extremely important and I would like to be able to extract as much as possible from them into UDM fields.
Thanks!