Hi there,
I am testing a detection rule with Zscaler, specifically trying to detect “malicious download” behaviors.
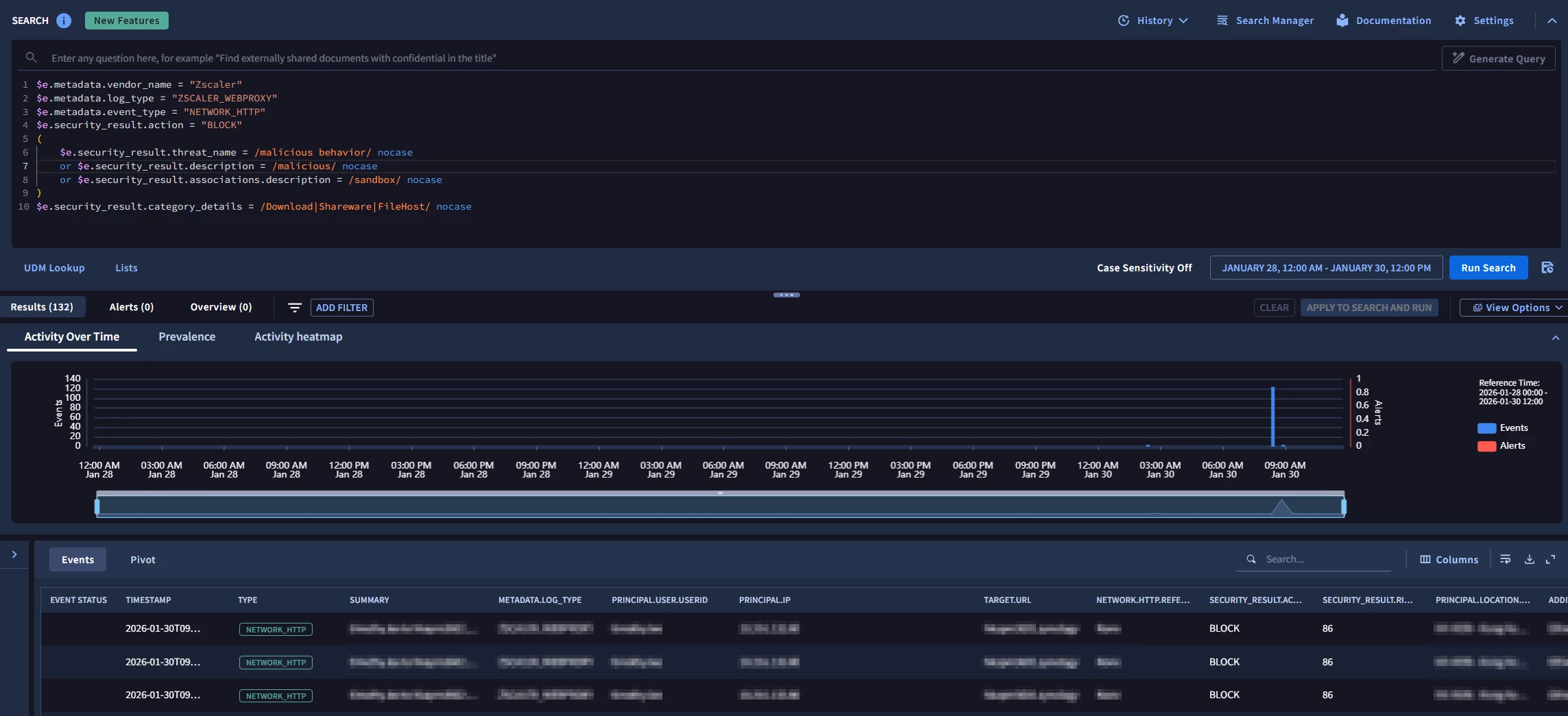
I have a simple single event query which returns results when ran in UDM search:
$e.metadata.vendor_name = "Zscaler"
$e.metadata.log_type = "ZSCALER_WEBPROXY"
$e.metadata.event_type = "NETWORK_HTTP"
$e.security_result.action = "BLOCK"
(
$e.security_result.threat_name = /malicious behavior/ nocase
or $e.security_result.description = /malicious/ nocase
or $e.security_result.associations.description = /sandbox/ nocase
)
$e.security_result.category_details = /Download|Shareware|FileHost/ nocase
However, using the same core logic as a YARA-L and with the same timeframe testing it with “RUN TEST”, I am getting no result:
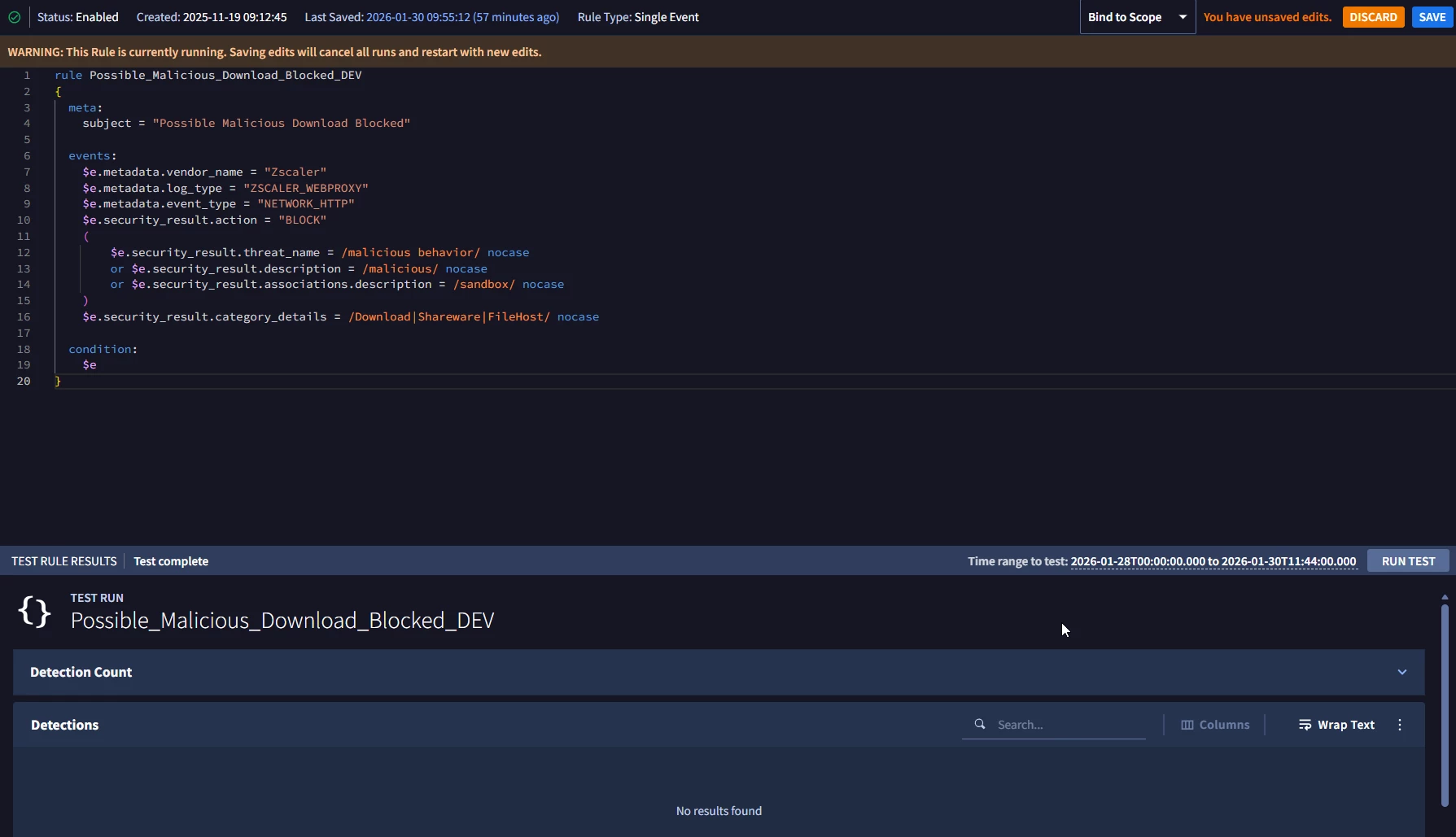
This post Detection Rule Test | Community seems to suggest data freshness as a potential issue but I don’t believe this has something to do with it as the events occurred more than an hour ago.
I’m new to SecOps and I would appreciate if someone could help me figure out what I’m doing wrong or if I’m missing something here, thanks!

